Three years ago today I had 3.2kW of solar panels and a 5kW battery installed on my home. Heating and hot water, currently, come from a gas combi boiler – boo! – but that’ll change…
Should you do the same and “go solar”? My experience would say ‘yes, absolutely’.
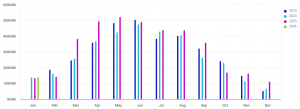
Over that three-year period my panels have generated 10.65MWh of electricity, nearly two thirds of which (65%) was exported to the grid. As you might expect over the course of the year much more electricity is generated (and thus exported) in the summer. Shorter days and overcast winter weather naturally means buying more grid power in the winter. Averaged out our consumed grid power has been directly reduced by more than a third (35%). Our usage is pretty consistent – we use an average of 12.9 kWh of electricity every day, all year round. At the average UK price of 27.69p per kWh, plus the daily standing charge of 54.75p, that would mean a daily cost of £4.12 if we had to buy it all. That would create an electricity bill in the region of £125.40 per month.
What effect have our battery and solar panels had on bills? The short answer: a huge one.
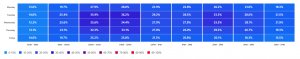
The more detailed answer is that the level of saving is hugely dependent on energy tariff. In February 2023 we were with Eon, who paid a miserly 5p per kWh of exported power at that time. As soon as I could I switched to Octopus Energy’s Flux tariff which improved things enormously – it has a cheap early morning slot to fully charge up the battery, allowing one to export power as soon as the sun comes up, rather than using the first few hours of sunlight to charge the battery. Then there is an evening peak rate where you can empty your battery to the grid and earn top prices for your saved power.
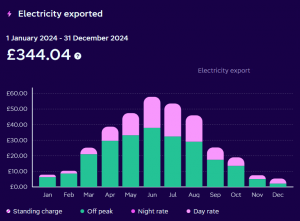
This bar chart shows my earnings for exported power during 2024, at the various time-of-day rates. I was very pleased with this: it cut my expenditure on electricity to under £264 for the year – which meant an average electricity bill of £22 per month.
But it turned out there was further room for improvement.
The Intelligent Octopus Flux tariff offers you the option to export power at exactly the same price as you pay when you need to buy it – which makes it the most generous export tariff on the market, at time of writing. The trade-off is that you hand over control of your battery to Octopus, so they charge it up when power is cheap, and export it to the grid when power is expensive. The aspect of this tariff that made me pause was that this meant losing the ‘Eco’ option, where your battery supplements current solar generation minimising your draw from the grid. I was very aware that this meant I would have to buy more electricity.
Despite those concerns, I switched to Intelligent Octopus Flux at the end of April 2025. Sure enough, my imported electricity bill did indeed go up, by about 20%. But this was more than offset by the enormous difference of exporting power at rates in excess of 20p per kWh.
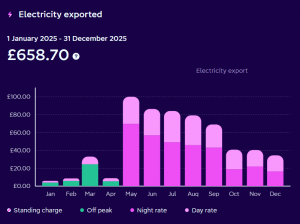
Immediately my earnings soared – by the end of 2025 my income from exported power was close to double what it had been for the year before. I found myself wishing I had switched tariff sooner.
On this new intelligent tariff my net electricity bill for 2025 was thus even lower than 2024’s – a total of £195.79 for the whole year: an average of £16.32 per month. I should also note that daily standing charges make up around £15 of that monthly bill.
My intention to remain on Intelligent Flux for the whole of 2026 should mean that my electricity bill for the year is lower still, perhaps even negative, once the government’s £150 reduction is applied to bills in April.
Future plans are to replace my gas boiler with a heat pump, and my petrol car with an electric one, so that I can save even more.
But I feel that I should add that while these savings are real, and very much appreciated, I also gain huge personal satisfaction at the environmental benefits as well as the financial saving – fossil fuels were used to generate over 28% of the U.K.’s electricity over the last year, emitting 127g of carbon dioxide per kWh generated.
My personal power-generation footprint is negative. It is estimated that solar panels offset the carbon cost of their manufacture and shipping within 1½ years, for Chinese-made panels, so mine are already well beyond that, with a remaining expected lifetime measured in multiple decades. Figures I found for my battery estimate 40 to 60kg of carbon costs per kWh of battery capacity: so worst-case 300kg. My combined system is estimated to have offset 2,208kg of carbon dioxide to date – again, making me feel comfortable that I’m into negative carbon territory. Finally, Octopus Energy themselves supply only renewable energy – even the power I do have to buy is as ‘green’ as possible.
Octopus don’t just buy power on the open market, they also generate their own electricity, including owned wind turbines in East Yorkshire, Hampshire, Somerset and South Wales, power bought from Co-Op Community Energy, and more locally to Oxford, they buy power from the first community-owned hydro scheme on the River Thames, at Osney Lock, and from over 500 panels installed on Oxford Bus Company’s HQ roof.
If this has inspired you to consider switching to them I do have a referral link that will earn you £50. 😉