Late yesterday we agreed and released a Microsoft patch (KB3050265) to all of our managed machines. This resolves a known issue whereby in some circumstances the machines resources get eaten up by a rogue svchost process whilst it is analysing which updates are installed and/or needed. Our testing this week has proved successful and we’ll be monitoring the progress of the updates and any noticeable changes closely.
For a while we’ve been taking a close look at the processes that run on desktop machines relating to Windows Updates. We use a Microsoft WSUS (Windows Server Update Services) server to manage and deploy Windows updates to all CONNECT managed machines. As noted in the previous blog post we’d spotted a specific issue that was occurring on some machines relating to the svchost processes taking a large amount of RAM. This was tracked back to the scheduled checks machines do every day to review their update status against the WSUS server. We’d been deploying a script to specific machines where we have seen this issue for a while however were also aware that this was very much a short-term fix, with the problems and symptoms often re-appearing on machines.
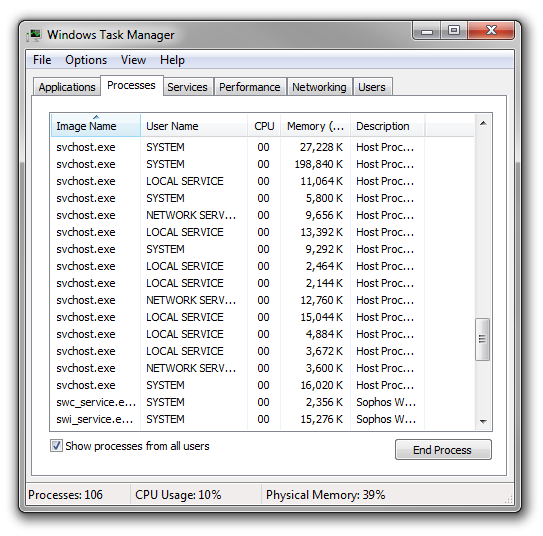
The Microsoft blurb describes the svchost as “a generic host process name for services that run from dynamic-link libraries”. In slightly more understandable terms Windows lumps together related system services and runs them as a svchost processes, so it’s not a one-one link between a service and a process but a group of services running together as one process. If you look at the list of processes running on a machine you’ll find a number of these running, some within the user instance and some running at system level behind the scenes. Here’s a screenshot from my PC showing this: